WazirX Hack Analysis

Overview
On July 18th, 2024, WazirX, India's leading cryptocurrency exchange fell victim to a ~$230 Million attack. One of their self-custodial safe multi-sig wallets was compromised and drained.
Main addresses and transactions
Main actors
- Victim: WazirX 📉
- Weak link: WazirX's signers ✍🏻
- other weak link: Liminal custody
- Hacker: DPRK-linked actors (Lazarus Group) 🇰🇵
- Vulnerable party: Safe 🔐
- Detector: Cyvers 🚨
- Investigators: Mudit Gupta & ZachXBT 🕵🏻♂️
- Mixer: TornadoCash🌪️
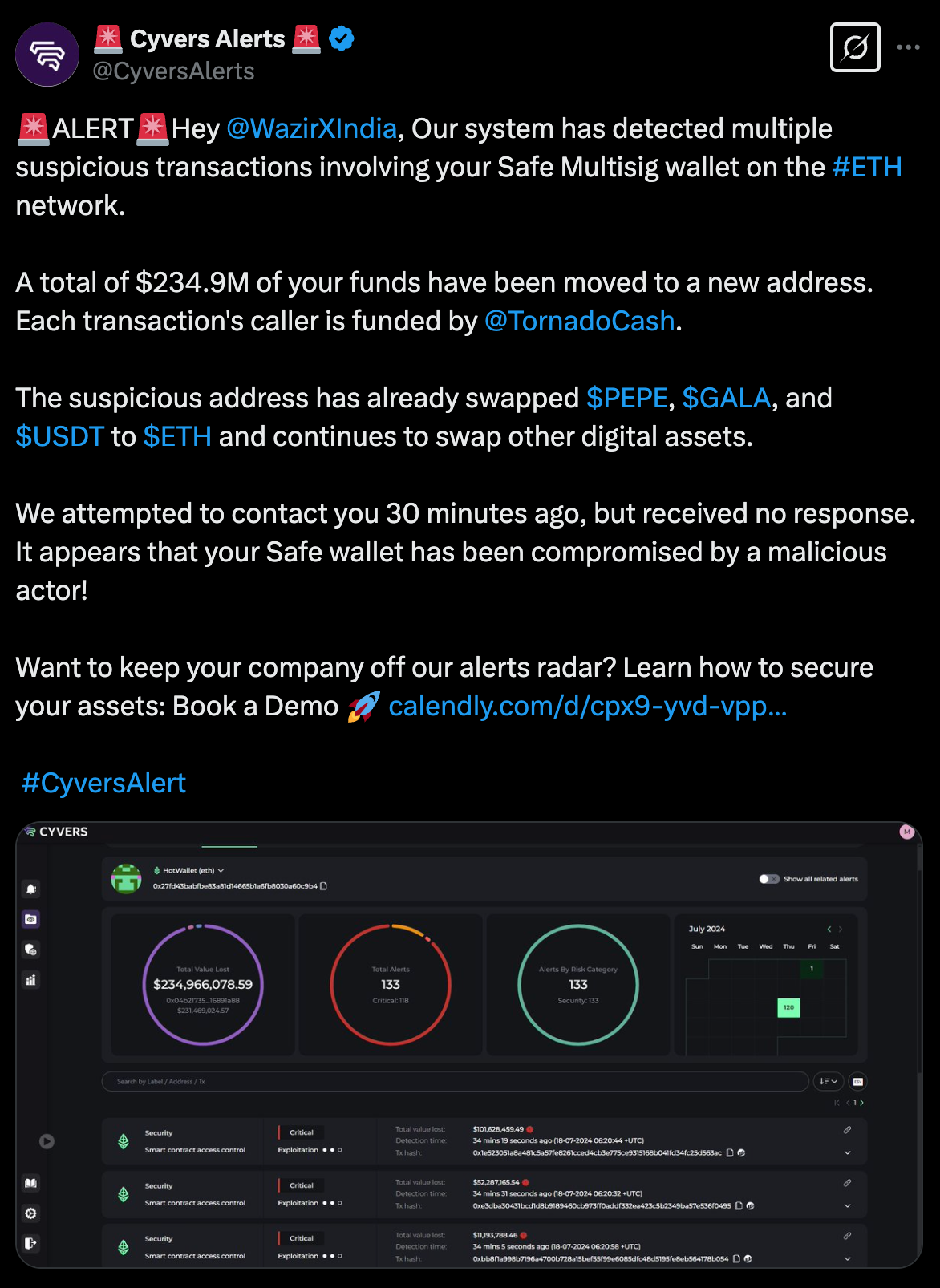
🚨Attack Detection🚨
- Suspicious Tx involving WazirX's Safe wallet on the ETH network
- $234.9M have been moved to a new address
- Tx callers are funded by TornadoCash
- Suspicious address has swapped numerous assets to ETH
- With no response for 30 minutes, Cyvers took it to X
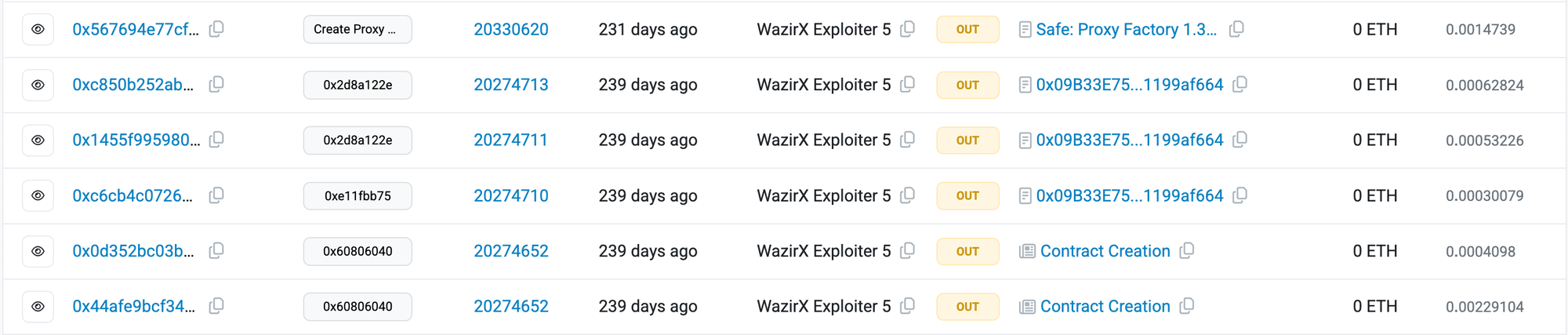
The attack at the smart contract level
- The hackers started practicing the attack for at least 8 days
- The wallet tried to do a USDT transfer minutes before the hack started
- ... But it failed because 2/4 signatures were for upgrading the safe to a malicious contract rather than USDT transfer
- The 2 signers were tricked into signing malicious tx in the name of a normal USDT transfer
- Once the tx was published onchain, it failed but the hackers got the signatures that they wanted as signatures are submitted publicly in tx
- The hackers then used the other 2 compromised private keys to generate 2 more signatures and successfully executed the exploit tx to upgrade the multisig to a malicious contract that transfers all funds to them.
- One of the 2 phished signatures is actually a pre-validated signature indicating that the `msg.sender` (co-signer from Liminal custody) authorizes the tx
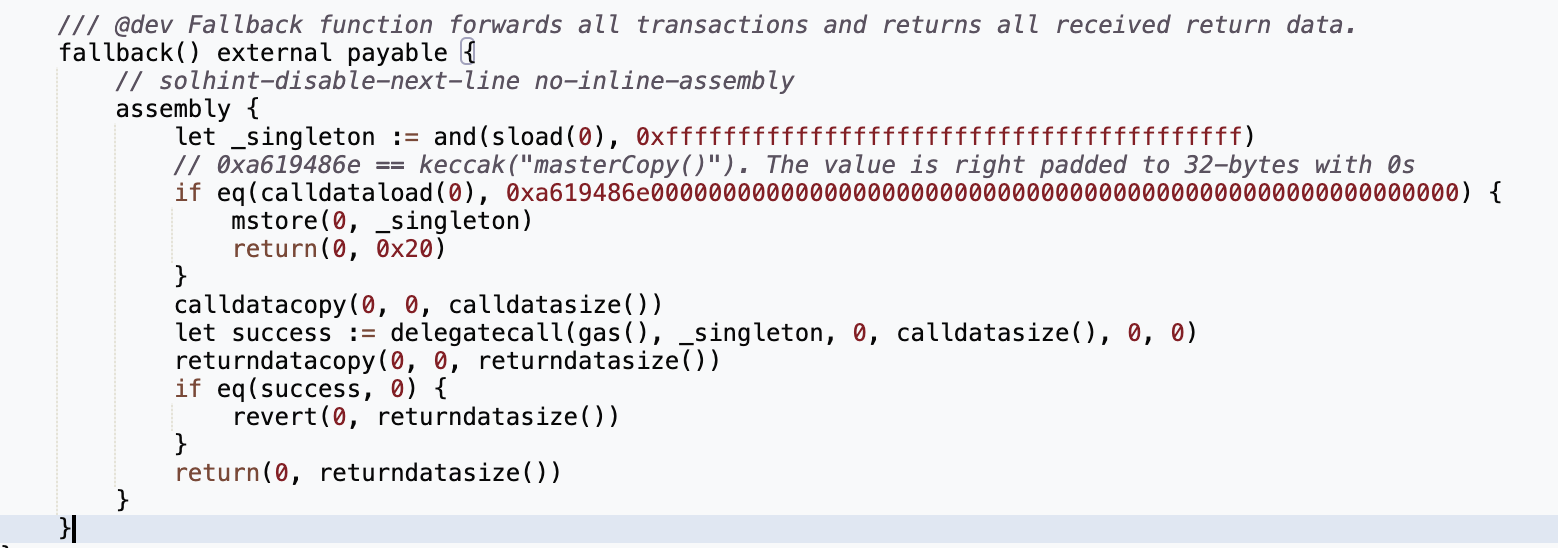
- The attackers upgraded the Multi-sig wallet to a malicious contract through a delegateCall()
- The delegate call targeted the function 0x804e1f0a, which modified slot0 of the multisig proxy storage
- Now, slot0 which stores the address of the implementation is storing that of a new implementation, the malicious contract
- It allowed them to drain the wallet from its funds as the new implementation contract was designed to transfer assets out of the multi-sig wallet
- Each tx to the multi-sig triggered a delegateCall() to this malicious contract, enabling continuous draining of funds.
🔐After (and even before) the 1.4B ByBit hack, X has been generous with best practices to prevent signer-level attacks from happening. Decided to gather them all in one place 🧵@shafu0x@PaulFrambot @PatrickAlphaC @pcaversaccio @alcueca @_SEAL_Org
— 0xjarix (@0xjarix) February 24, 2025
Check out this tweet to stay safe
Key Takeaways
- Smart contracts are starting to be very secured so hackers target weakest link: humans
- Safe's Front-end was vulnerable, it was confirmed through the bybit hack so web2 audits have to be better
- Signers should know what they're signing (|)0/\/'T TR|\_|5T, \/3R1FY!)

